Security and Privacy
Information security and privacy are not implemented once and forgotten, they are an ongoing process that is applied throughout the life of a device or service. And what works for a workgroup color laser MFP will be different from a home inkjet printer or industrial label printer. Since 1991, the PWG's goal has been to enable appropriate security and privacy processes and controls for every organization, environment, imaging device, and image service. Where appropriate, we also work with other standards organizations including the IEEE, ISO, and TCG to develop meaningful resources for developers of printing and imaging products.
The PWG has helped to develop ISO/IEC 10175-3:2000 Document Printing Application (DPA), IEEE 2600-2008 IEEE Standard for Information Technology: Hardcopy Device and System Security (P2600), and most recently the HCD iTC Collaborative Protection Profile for Hardcopy Devices to define standards and best practices for the secure and safe use of a Printer, Multi-Function Device (MFD), and/or Imaging Service throughout its lifecycle. The PWG has also defined standards for identifying and protecting personally identifying information (PII), including best practices for obtaining explicit consent before collecting or using this information and a standard that supports printing through untrusted intermediaries.
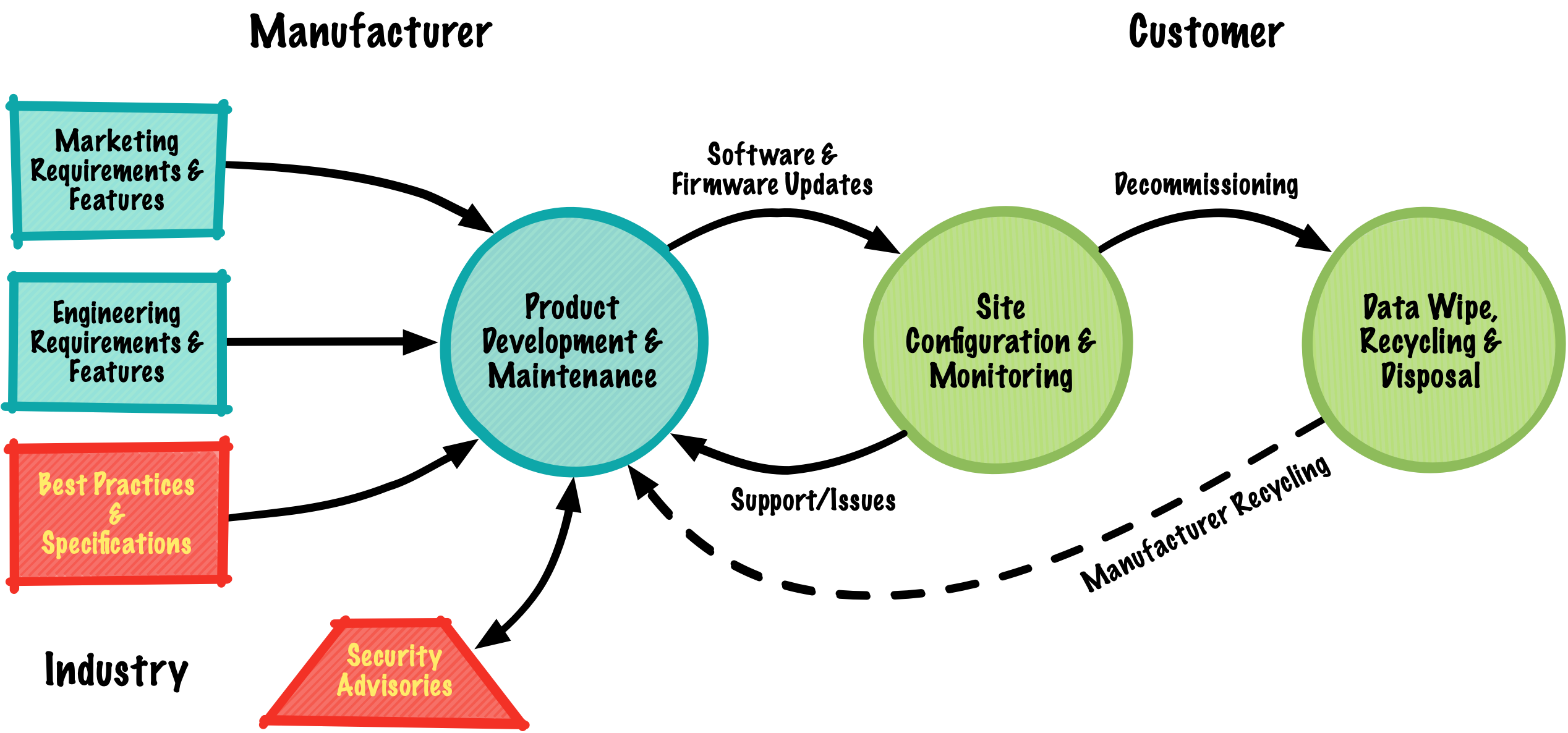
Security Lifecycle
Security requires engineering best practices and standards. Network products require regular and trusted firmware/software updates to address customer issues, changes to best practices and standards, and fixes for security vulnerabilities. When it is time to take a product out of service, customers need a reliable and secure means of wiping the product of any customer information so that it can be recycled and/or disposed of properly.
Basic Security Features
Printing and imaging products can adopt several basic security features:
- Platform Integrity Verification: Secure Boot, Self-Test
- Process isolation and trust: TCG Trusted Platform Modules, TrustedFirmware, Linux kernel security modules and code signing, virtualization and containerization solutions, etc.
- Network isolation and trust: TCG Trusted Network Communications, IPP Shared Infrastructure Extensions v1.0 (INFRA)
- Protection of data in transit: TLS, TOFU and/or site policies for X.509 server certificate validation
- Protection of data at rest: Encrypted storage/filesystems, TCG Self-Encrypting Drive Standads (OPAL)
- Confidentiality and data integrity: Use of strong cryptography, IPP Encrypted Jobs and Documents v1.0 (TRUSTNOONE)
- Automatic firmware/software updates
- Protected audit logging and accounting: PWG Common Log Format, PWG 5199.11-2021: Job Accounting with IPP v1.0
- Identification, authentication, and authorization: X.509 client certificates, IPP Authentication Methods
A typical network printer supports TLS to protect data in transit, uses a self-encrypting SSD or hard disk to protect data at rest, advertises its privacy policy and configuration using the IPP Privacy Attributes, limits access to authorized users using IPP Authentication Methods, and provides audit and accounting logs using the PWG Common Log Format standard and Job Accounting with IPP best practice:
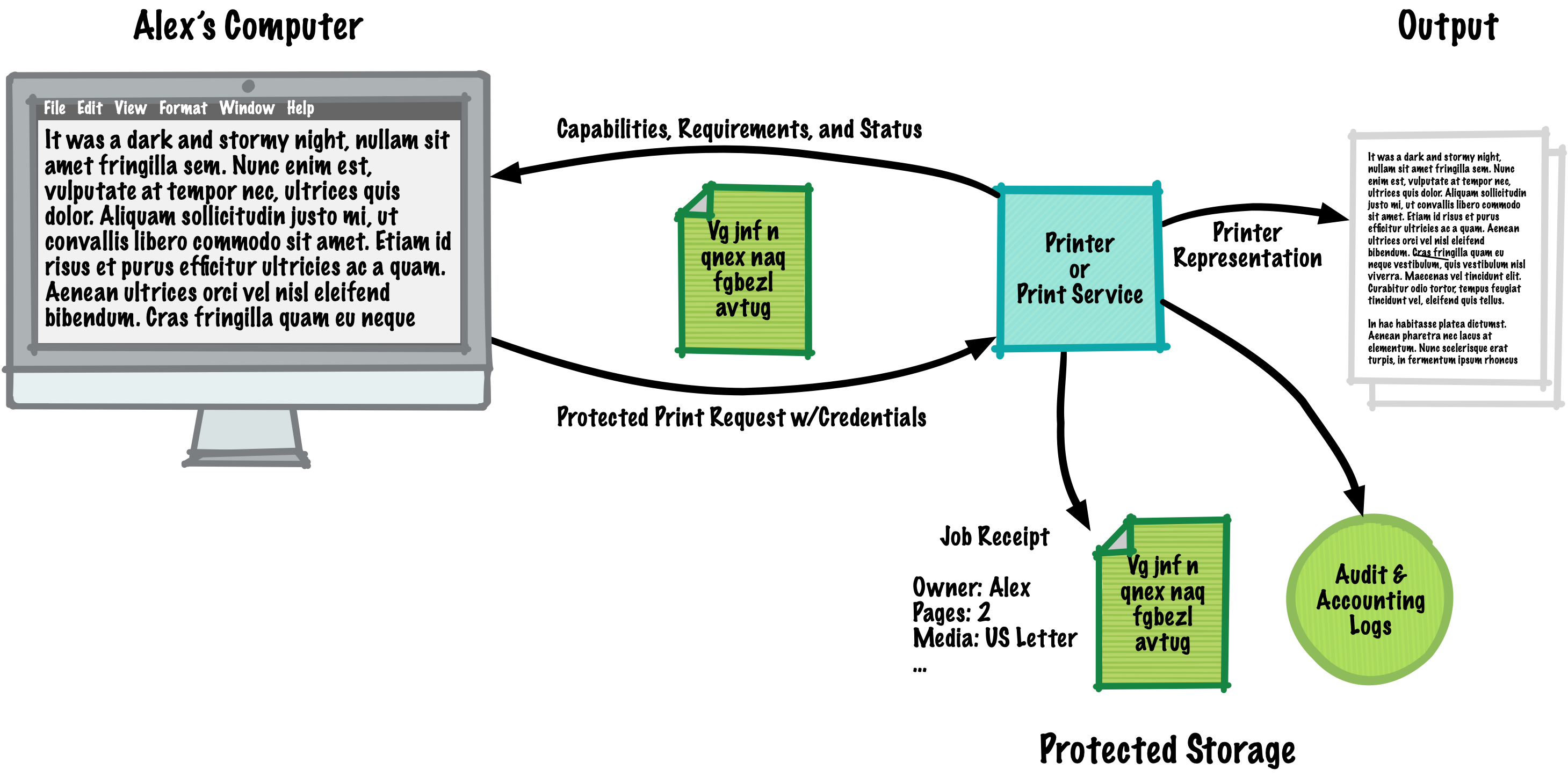
Reliability by Design
Reliability comes naturally with proper design and implementation:
- Intent-oriented design, both for protocols and file formats: what you want to print, not the steps to perform on the Printer to make it happen
- No direct machine control: a client can't cause a fire or mechanical damage, bypass safety interlocks, or otherwise cause harm
Privacy
Printing necessarily involves Personally Identifiable Information (PII) that needs to be protected:
- Identification of privacy data and definition of site policy - IPP Privacy Attributes v1.0 (PRIVACY), NIST Privacy framework, and NIST SP800-53 Security and Privacy Controls for Information Systems and Organizations
- Use of privacy data, explicit consent - PWG 5199.11-2021 Job Accounting with IPP v1.0
- Protection of extremely sensitive information - IPP Encrypted Jobs and Documents v1.0 (TRUSTNOONE)
- Regulatory Compliance: European Union General Data Protection Regulation (GDPR), California Privacy Rights Act
Resources
PWG Standards:
- IPP Shared Infrastructure Extensions v1.0 (INFRA)
- PWG 5110.1-2013: PWG Hardcopy Device Health Assessment Attributes
- PWG 5110.2-2013: PWG Hardcopy Device Health Assessment Network Access Protection Protocol Binding
- PWG 5110.3-2013: Common Log Format
- PWG 5110.4-2015: Hardcopy Device Health Assessment Trusted Network Connect Binding (HCD-TNC)